how long does it take to reset end to end encrypted data
Asymmetric encryption requires the use of both a public and a private key. The endpoint that did not initiate the TLS connection.

What Happens When You Reset End To End Encrypted Data Iphone
The following examples show the differences between end-to-end encrypted confidential emails and emails that are not being end-to-end encrypted in Tutanota.

. There are no tools similar to it so the fastest way to see what it does is to see 5 things only WP Reset does. Replaced by MAV_FRAME_LOCAL_FLU 2019-04. As a result the entire data for the 3rd quarter is pending to be.
My 237 GB SSD disk took nearly 3 hours. Trying to use adb input keyevent to mimic the key presses. Theyre going to raise rates in 2022 Higher rates could help.
WhatsApp Starts Rolling Out End-to-End Encrypted Cloud. In the case of multiparty meetings all audio and video traffic is still encrypted on the network again using DTLS-SRTP. Some personal data such as Home and Health data is stored with end-to-end encryption which provides the highest level of data security.
The benefit of end-to-end encryption is that response data enters and remains in Forms servers in an encrypted state. Stocks end lower after mixed jobs data as tech sinks again. The typical TTL for local files is 7200 minutes 5 days but is less for files on other media like a network share.
This kind of selective use of childrens safety as a political tool makes it extremely clear that for them its not really about childrens safety its about furthering an agenda of increased surveillance and. If the end-users data is split among two or more server nodes and work is still possible when one of these nodes goes down or off the network then multiple server nodes can be employed. Email encryption is needed whenever you want to send a confidential email.
An endpoint that is transmitting records. The encrypted data is sent to the recipient. No one else can access or read this data.
If the data is larger than this size libcurl which handles the HTTP support for Git will use chunked transfer encoding since it isnt known ahead of time what the size of the pushed data will be. These definitions are reproduced at the end of this topic. WP Reset is a time saving tool.
In the beginning of the 3rd quarter we began the process of migrating to another internet service provider. Wiping the data myself using rm -r on the folders its supposed to do datacachesd-ext etc. In this case audio and video are encrypted using DTLS-SRTP all the way from the sender to the receiver even if they traverse network components like TURN servers.
This year CWI is celebrating. NetApp Volume Encryption NVE is a software-based data-at-rest encryption solution available starting with NetApp ONTAP 91 management software. See how it works.
Instead the cache has a TTL time to live and once expired the file is scanned again. Usually there isnt a Trust DAT change and so the cache isnt reset. At then end Abellas squeeze his black dick so good with her pussy that he.
75 Years ago the institute opened its doors. P2P mode is only used for 1-to-1 meetings. This does wipe but then the ROM doesnt work properly and gets stuck in a bootloop.
In the long run. Leaving this value at the default size is fine unless you know that either the remote server or a proxy in the middle doesnt support HTTP11 which introduced the chunked transfer encoding. By default Tutanota automatically encrypts subject body and attachments something PGP does.
This ensures that even if our servers are compromised by an attack attackers will still not be able to decrypt and view your response data as they do not possess your secret key. This is the main use of a public key to. This error simply means that the other side.
Encryption is a mathematical process used to jumble up data. Why sanitisation is necessary the risks to manage and how to sanitise affordably. At some point they take turn riding him bouncing their big asses on his cock like theres no tomorrow.
ECONNRESET means the other side of the TCP conversation abruptly closed its end of the connection. Research within CWI is organized in 15 research groups. Kate Bevan katebevan.
This data is protected with a key derived from information unique to your device and combined with your device passcode which only you know. Tap Factory data reset. It has a long history in cutting edge research as the birthplace of the open Internet in Europe the Dijkstra shortest path algorithm Python and much more.
WhatsApp Indicators for End-to-End Encryption on Calls Status Spotted to Be in the Works. Looker continues to pursue security certifications that matter to our customers. Odometry local coordinate frame of data given by a motion capture system Z-down x.
We had synchronized data with HO till the end of the 2nd quarter of the current financial year. Does that mean plotting Tories will stop using WhatsApp which is er also end-to-end encrypted. Tutanota is even unique in the fact that you can send end-to-end encrypted emails to any email provider via a shared password making the email just as private even when contacting friends family and business partners using mainstream providers like Gmail.
Answer 1 of 4. If important files or whole devices are encrypted there is no way to make sense of. 12Major Differences from TLS 12 The following is a list of the major functional differences between TLS 12 and TLS 13.
NVE also allows customers to use storage efficiency features that would be lost if the customer. Pussy to mouth to mouth to pussy and back again. Business intelligence security is a top priority We are driven to build a data platform that scales with the exponential growth in volume and demands for dataand meets the growing need complexity and importance of data security.
This reset is so that the new trust information removals and additions can take effect. Some applications of public key technology include the following. The two girls almost gets more than they bargained for as he pounds them in almost every position possible never showing a sign of fatigue.
If all the end-user data is on a single file server then there is no need for redundant servers and GLOBEtrotter Software recommends the use of a single server node for the FLEXlm daemons. Answer 1 of 7. Samantha Floreani samfloreani.
While the process of migration was in progress the branches were unable to perform synchronisation with HO. NVE allows ONTAP to encrypt data and to have that data stored on disk without requiring self-encrypting drives. That is whenever your email contains personal information that should not become public.
If you spend most of your days in WP admin youll realize it fills a need you didnt even know you had. RFC 8446 TLS August 2018 receiver. MAVLink 2 messages have an ID 255 and are marked up using MAVLink 2.
It is not intended to be exhaustive and there are many minor. The recipient decrypts the message using their own private key. I have no idea what they are mapped to because they are in a UNIX shell basically and even then there.
An endpoint that is receiving records. To check how much has been completed open command prompt - Admin and enter manage-bde -status.
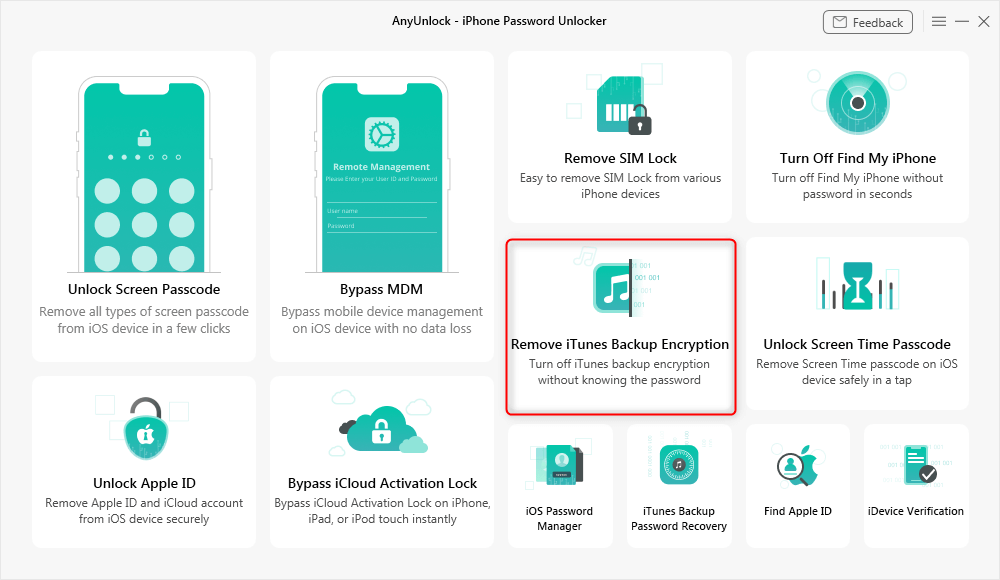
What Does Reset End To End Encrypted Data Mean
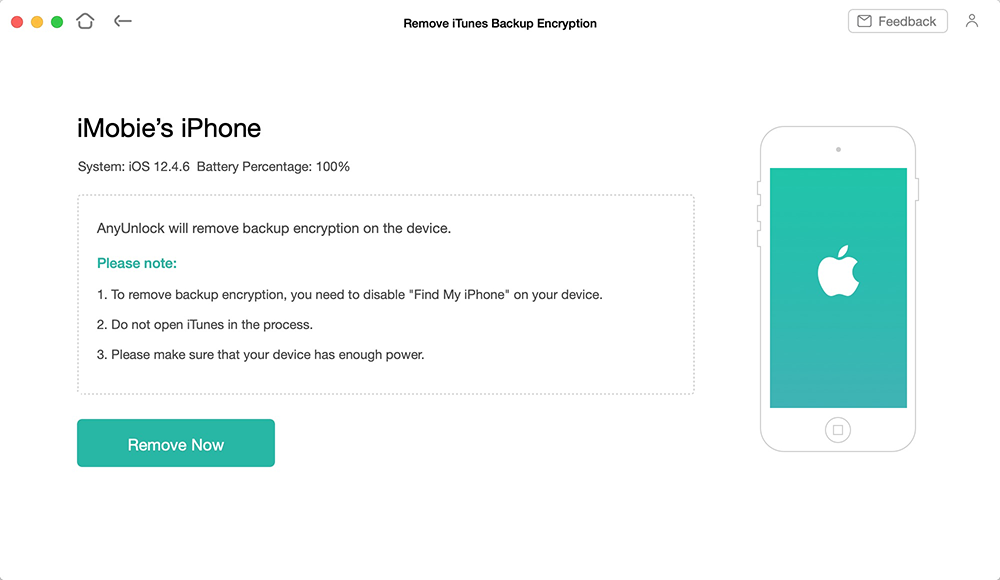
What Does Reset End To End Encrypted Data Mean

What Happens When You Reset End To End Encrypted Data Iphone
Updating Apple Id Apple Community
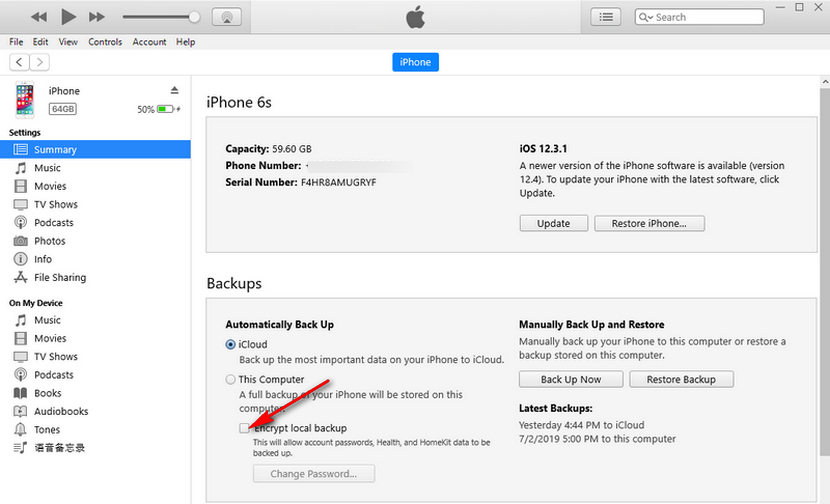
Best Ways To Reset Encrypted Data Iphone
End To End Encrypted Data Apple Community
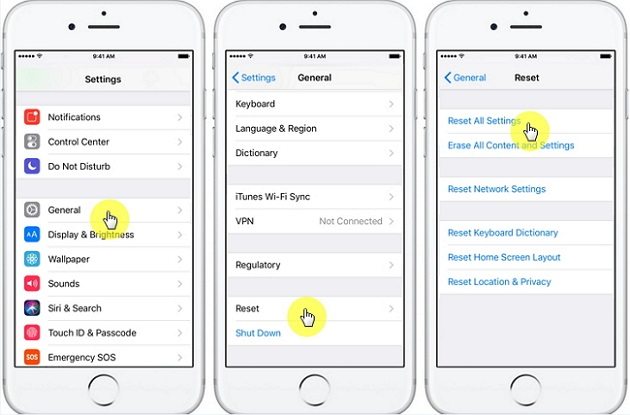
Best Ways To Reset Encrypted Data Iphone